The Challenge
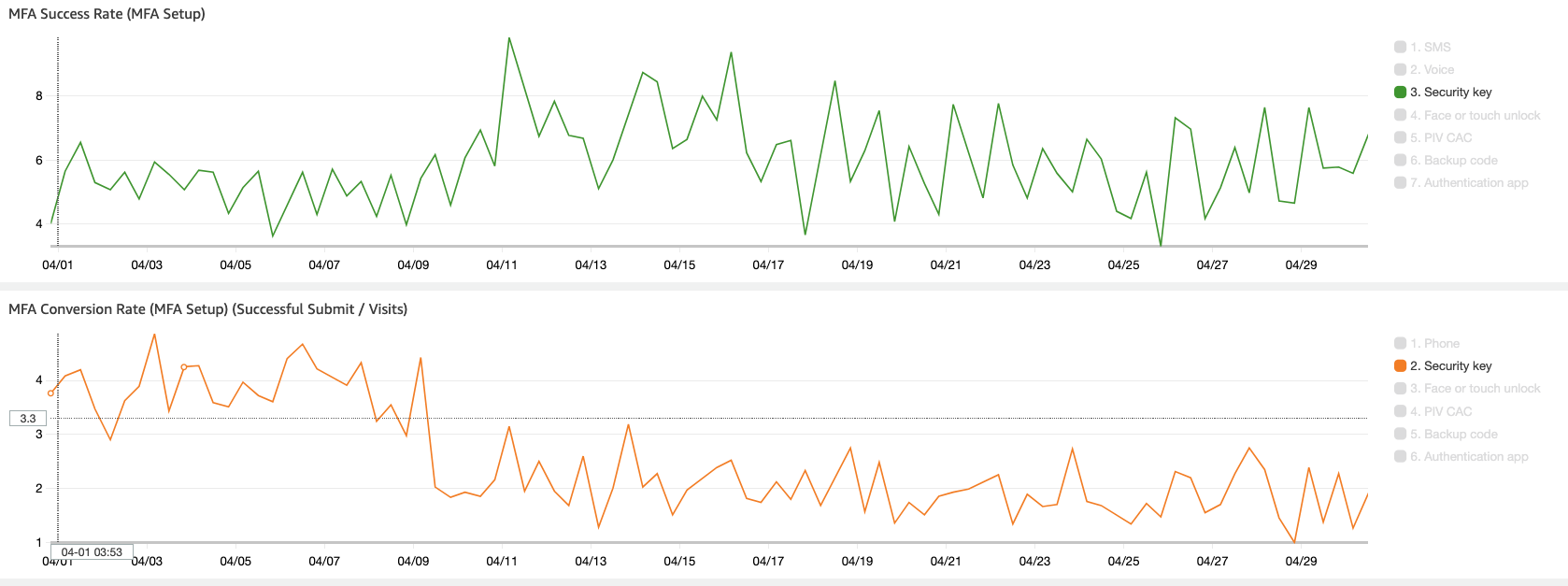
In November 2023, only 12% of active users employed phishing-resistant methods, with 78% relying on phishable SMS one-time passcodes. By February 2024, just 66% of security key users successfully authenticated within two weeks.
We sampled 1,298 support tickets between January 21, 2023 to January 20, 2024 and found three key themes:
- Process issues (433 tickets, ~33%): Issues ranged from users being unfamiliar with security keys to not having access to one when signing in.
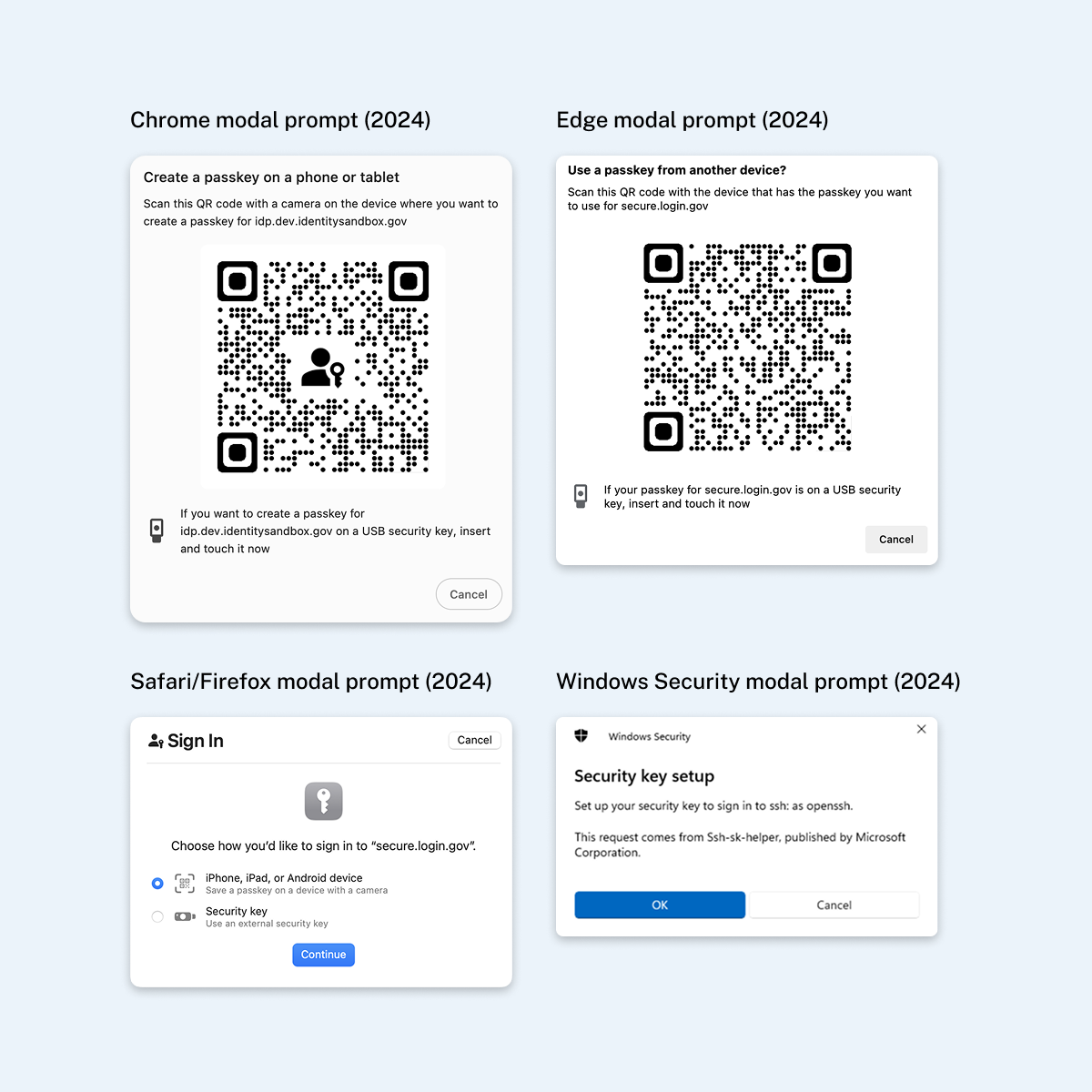
- Multi-factor authentication (320 tickets, ~25%): Many security key tickets seemed mislabeled as other MFAs. There was a high number of face/touch unlock (passkey) tickets mixed in due to shared systems messaging.
- Various codes (256 tickets, ~20%): Login.gov has a variety of different codes, and for some users it's not clear what they are or what they do. This adds to additional confusion on top of some of the long processes users go through for account creation, identity verification, and account reset.
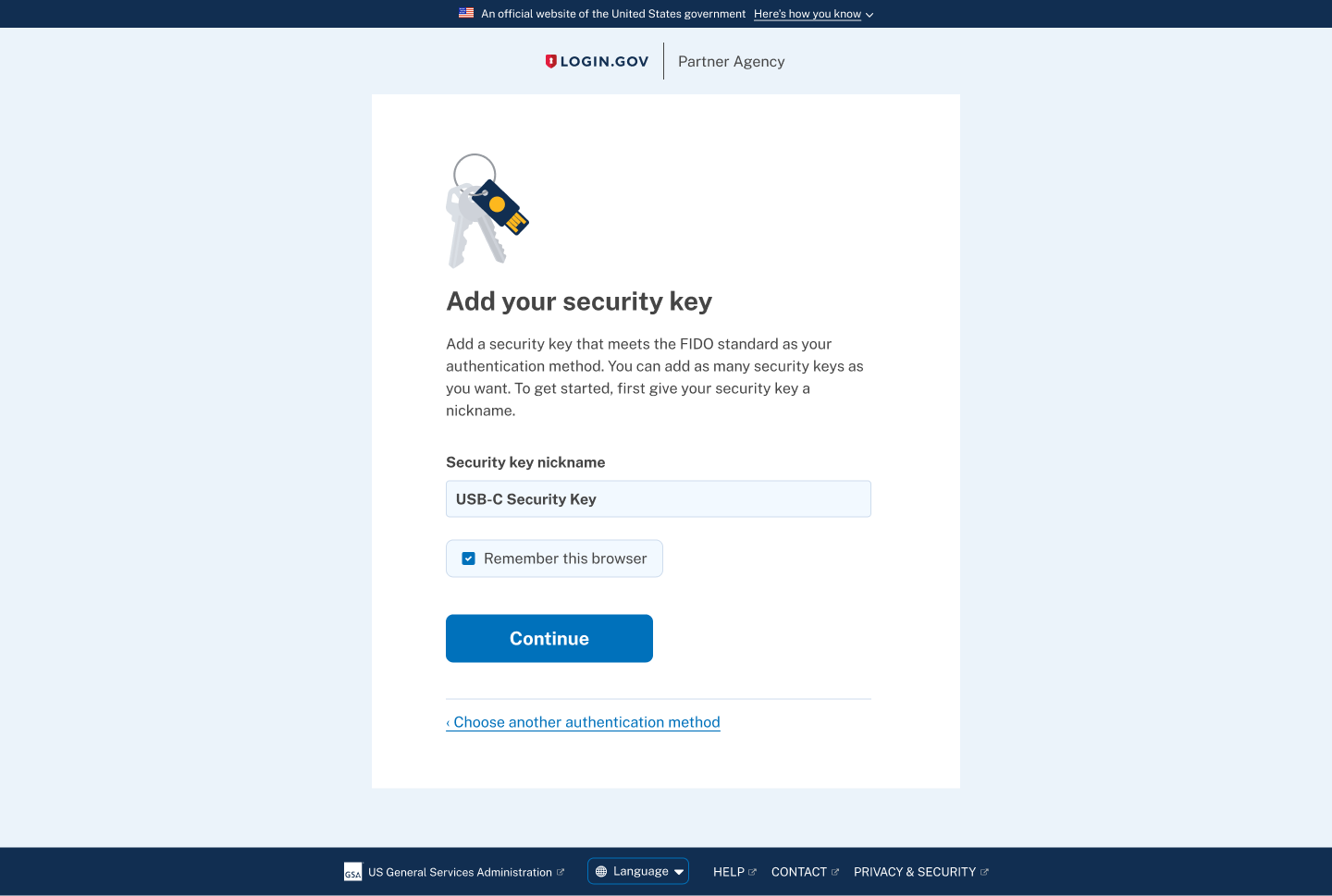
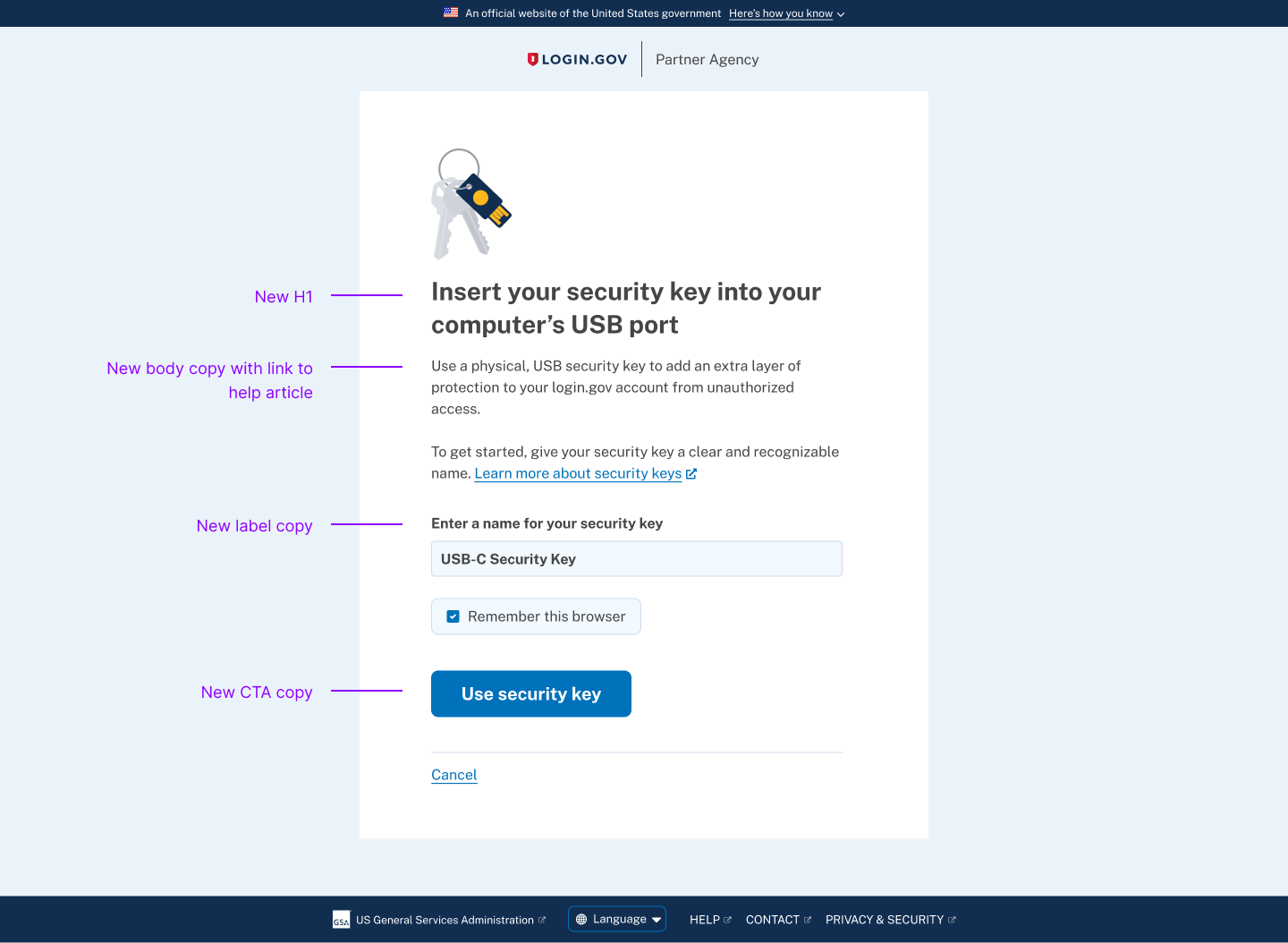
The original security key setup page included a vague H1: "Add your security key", which wasn't specific enough to the authentication method since all the other methods used the same language of "add x method". The paragraph below the H1 mentions FIDO standards which is not an important detail for the average user, adding to information overload.