Part 1: Outcomes & Impacts
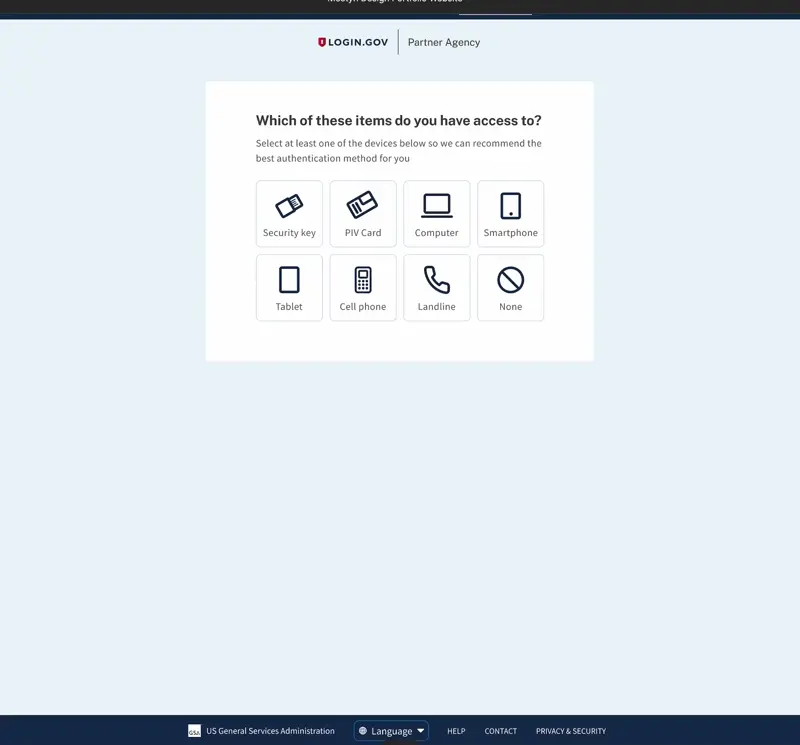
We selected the "Illustration" authentication page, despite good feedback for both options, since participants felt it offered better upfront context. The "Questionnaire" was less successful, as some participants found it unclear about the nature of each device.
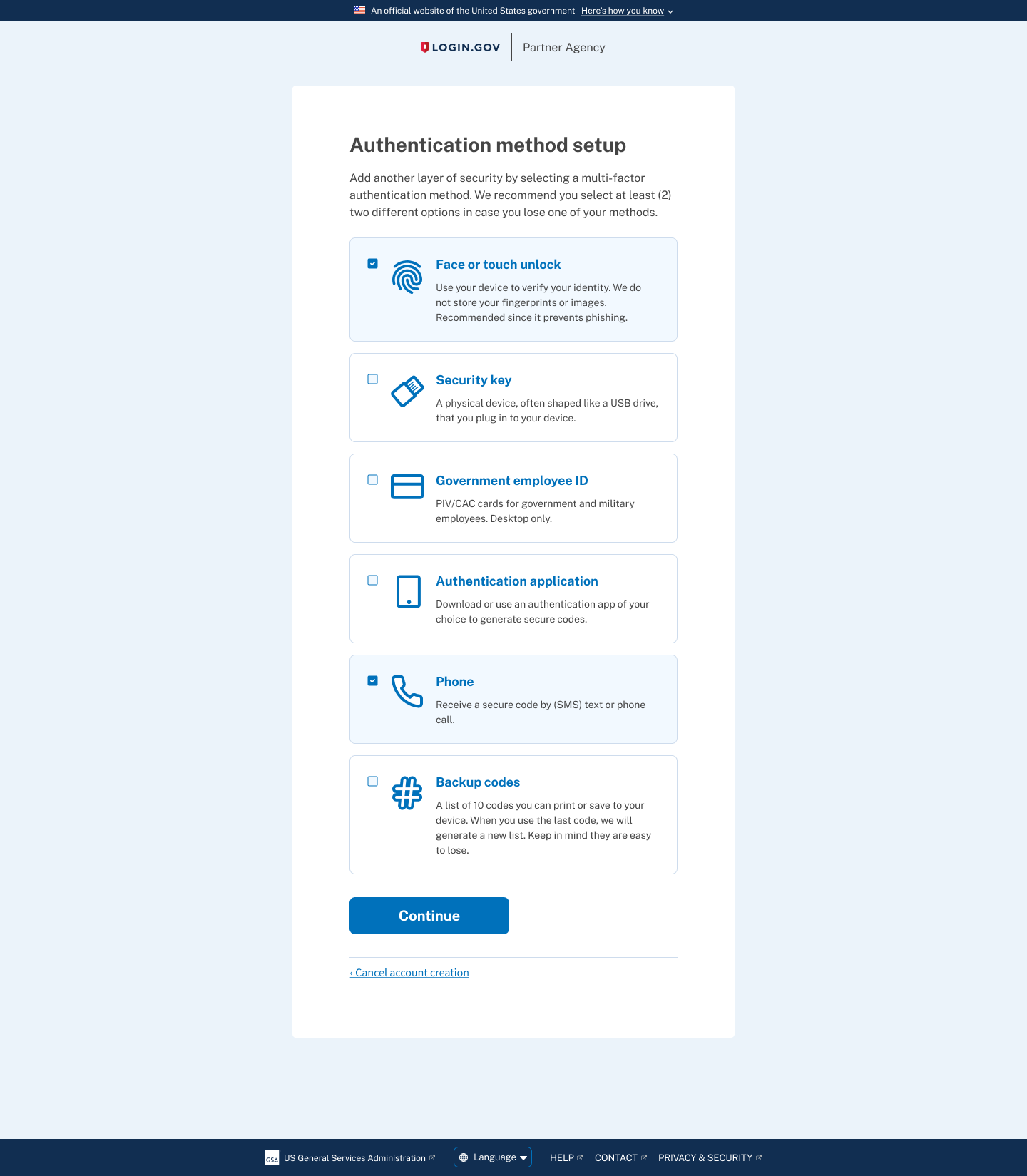
From January to February 2022 there was an 83.7% account creation success rate. In March 2022 there was an improved 92.8% success rate after the launch of redesigned MFA setup page.
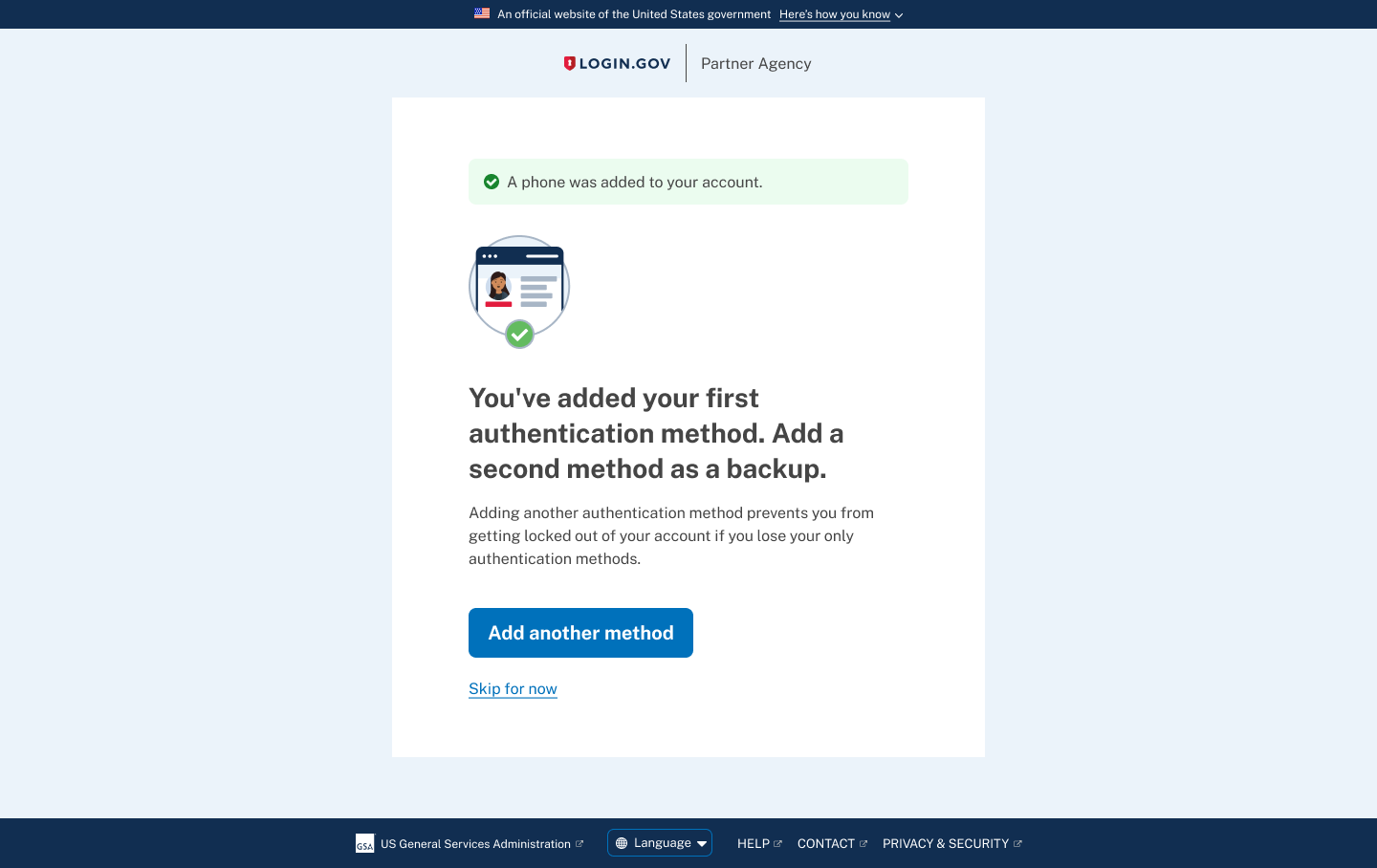
Though improving comprehension increased successful account creation, research and support data showed a second failure point: users who only set up one authentication method were still vulnerable to account lockout.